Anti Netcut
Anti Netcut : Keep your Internet connection constantly up and running as well as heavily guarded by this powerful and lightweight software applicationSometimes even a correctly-configured protection suite that includes an antivirus solution and a powerful firewall might prove to be insufficient when it comes to efficiently defend a computer from attacks from the Internet. In this case, one can try a dedicated tool for protecting the Internet connection rather than the PC. This is where Anti Netcut comes in handy.
Making sure are prerequisites are installed
The application is meant to guard the Internet connection when the target host is assaulted by NetCut, Arp Spoofer or ARP spoofing weapons that might, in the end, disconnect the machine from the web.Before actually installing this application, the setup will make sure the computer has all the needed software in order for it to run smoothly. Otherwise, it starts installing the requirements before launching Anti Netcut, and this is expected behavior, so users are advised to allow it to complete the install.An automated configuration process
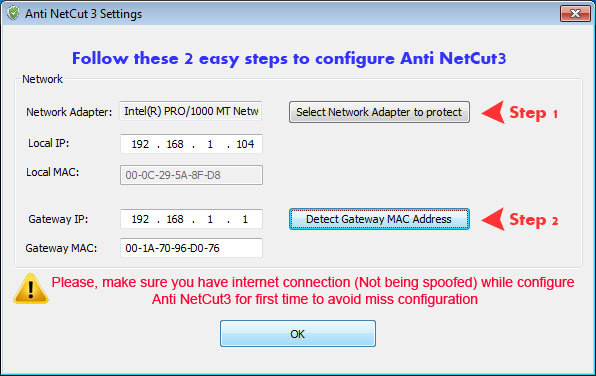
Before using the functionality of Anti Netcut, one needs to configure its settings, specify the network adapter that needs to be protected, as well as enter the gateway MAC address. Novices are likely to get confused by these terms, so the app features the option of automatically detecting the ideal settings, without any additional input from the users.View and resolve security threats
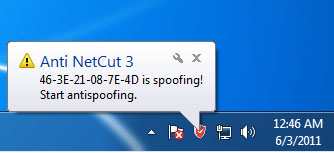
The developers probably considered that simplicity is the best path to success, so Anti Netcut sits quietly in the system tray, without bothering the user or displaying too many notifications. Right-clicking the tray icon allows users to view who tried to take down their Internet connection within the past few days, then restore the original settings in case something went wrong.Anti Netcut protects your computer connection from arp poisoning and arp spoofing attacks while working on shared computer networks (LANs) Anti Netcut prevents any buffering on the network which might affect the system functioning. It is a top with less complex functions and can be used by any user. In addition, the main window has minimal functions which allow you to use it with just a simple touch of a button.
Anti NetCut 3 will work in the back ground and detect any attackers that trying to cut or sniff your data connection then it will display a warining message and start anti spoofing technique to protect your network connection and protect your online privacy
Why Anti netcut 3
No internet disconnection any more.New enhanced anti spoofing techniques.
Starts with operating system , you don't have to run every time turning on your PC.
Know and log who is cutting your connection.
Protect all your network connections including WI-FI in one place.
No network knowledge required.
Protects your online privacy.
What is ARP Attack ?
When computers exchange data with each other, the so-called IP-address comes to play. It is a logical address, to which data packets are sent. Next to this, each computer - or more correctly its network card - has an unique physical address, the MAC-address. The ARP-tables define the connection between these two addresses (ARP = address resolution protocol). Each logical IP-address has its physical MAC-address counterpart.If any of these table entries are exchanged, so-called man-in-the-middle attacks become possible. This means that data streams are routed unnoticed via the attacker's computer. Here the data can be read or manipulated.
In the meantime there are even attacking tools available on the Internet. Every skilled network administrator can execute professional ARP attacks. Without any precautionary measures by the organisation that is running the network, the risk for the attacker to become unveiled is close to zero.
Encryption, like used e.g. with online banking, is not offering any protection against ARP attacks. ARP spoofing attacks are operated either from within the network, for instance by employees or contractors, or a small device can be installed within the network and the attacker controls this device remotely.
Placing the network device does not require any specific skills, cleaning personnel or housebreakers are sufficient. ARP spoofing is a particularly refined method to attack computer networks of all kind. It should be noted that attacks of this kind are almost impossible to detect.
Anti netcut 3 Alternatives
Stop CutProtecting the information stored onto a computer and keeping private things confidential requires some dedicated utilities that are not limited to antivirus or firewall programs. For example, securing an Internet or network connection and preventing external intrusions can be achieved by means of a small but efficient tool like Stop Cut.
Keeping data safe in a network
Essentially a system tray application which runs in the background, this particular software solution targets ARP spoofing attacks and network scanners that try to intercept or stop the data traffic on your LAN.
Basically, Stop Cut acts like a shield for situations like that when someone tries to spoof or copy the MAC address of the server, gateway or of your personal computer in order to capture the information you send and receive.
ARP AntiSpoofer
Spoofing, is a means in which someone can hide an application or command that is meant to interfere with your network's security even allowing them to route your Internet traffic to the attackerís computer.
ARP AntiSpoofer is a lightweight tool that offers you the means to detect and withstand Address Resolution Protocol spoofing.
User-friendly interface
ARP AntiSpoofer displays a comprehensive interface and makes all its functions available in the main window. Its straightforward approach makes it easy for you to choose the network adapter, set the local and Gateway IPs, toggle the ARP Helper and enable remote control.
Auto detect spoofing
ARP AntiSpoofer is capable of automatically recognizing an ARP spoof attack as well as a bidirectional antispoof. Once youíve finished the configuration for the utility, it can identify an attack and send antispoof packets that are needed to protect the getaway. Moreover, if you're dealing with a large number of attacks, you are able to increase the antispoof packet rate, covering all the hosts.
Easy to configure
As long as you know what youíre doing and have all the information you need, ARP AntiSpoofer is a cinch to setup. You can choose the network adapter, set the subnet mask of the network, bind the IP and MAC addresses, enter the time between the sent antispoofing packets and their validity. You are also able to use it remotely after you provide a port number and login password and have ARP AntiSpoofer display notifications when spoofing occurs.
Protect multiple hosts
Though light, ARP AntiSpoofer is capable of offering security for more than one host. It allows you to enter the IP and MAC addresses of the hosts and displays them all in a table so you can see which ones have host or gateway spoofing activated.
ABM net protection
Most users are not aware of the risks they expose themselves to when connecting to the Internet through unprotected networks, like public ones. ABM Net Protection has been created to provide a minimum of protection against some methods that could result in losing sensitive information.
Installation pre-requisites
The application installs quickly and it requires WinPcap in order to function; this is a standard tool for accessing the network at link layer under the Windows environment.
Unfortunately, this pre-requisite is not provided on all operating systems during the installation procedure of ABM Net Protection. On the other hand, you are informed of the necessity of WinPcap when trying to launch the application.
Minimalist interface with no settings to tinker with The interface is simple and there are no settings to tinker with. Once started, ABM Net Protection should keep your system safe against attacks such as ARP (Address Resolution Protocol) poisoning, which consists in an attacker sending spoofed ARP messages to the local area network. This results in taking over the MAC and IP address of the target so that all traffic is diverted to the attackerís device.
Another security measure provided by ABM Net Protection is to stop packet sniffers, which intercept the traffic exchanged over the network and thus offer access to all the communication, unless it is encrypted.
The tool also claims to be able to stop spoofing attacks and the application window shows the gateway as well as the local IP and MAC address of the system.
Stop ARP poisoning and protect your system
ABM Net Protection basically connects to the router and collects the necessary information about the system and tries to keep it safe from attacks.
XArpG
The XArpG application provides a GUI (Graphical User Interface) version of network management small tools. XArpG is a applied to the LAN environment, network management tools. GUI (Graphical User Interface) version of the XArpG and CUI (Character User Interface) version of the XArpC together form XArp tool suite. XArpG to help network administrators to manage networks, resolving network problems. XArpG is base on IPV4 and Ethernet network. Such as PPPoE for ADSL is not currently supported; for other non-Ethernet network environment is also being not support it. Fewer people use IPV6 currently, so there is no program code for the IPV6 protocol in XArpG internal.
Netcut-Defender
Netcut-Defender is a compact tool that aims to protect your network connection from spoofing attacks. It is designed to stop the ARP spoofing attacks when unauthorized users impersonate your computer and use it to send data packets.The ARP spoofing attacks are meant to cut-off your Internet connection or to drastically reduce its speed. This tool enables you to find which computer from the network was attempting to use this technique on you and to cancel its effects.
You can successfully use this tool if other users from the network are attempting to impersonate your computer with the netcut application. It does not require any configuration after it is installed on your computer.The interface is easy to use and allows you to select the network connection that you want to protect if you are using multiple adapters. You can check the connection and reload the application components if the protection is not working.

How to Prevent ARP Spoofing Attacks?
Address Resolution Protocol (ARP) and its spoofing attacks are nothing new in the world of hacking threats, but history sheds light on why these types of attacks are so common. ARP was first developed in the 1980s for networks to manage connections without an individual device attached to each. Although this can make it easier for two machines to connect more efficiently and freely to transmit information, it also leaves your data wide open to vulnerabilities and theft.Security is a pervasive problem when using ARP. Also known as ARP poisoning, ARP spoofing is a cyber attack that is carried out over a Local Area Network (LAN) that sends malicious ARP packets to a default gateway on a LAN. The purpose is for attackers to disguise where their IP address is coming from so they can attack your devices for malicious purposes. And because they are concealing who they are, itís not always easy to detect the malicious activity until itís too late.
Although each ARP spoofing event follows a similar attack process, they can vary in how they access your devices. Determining which attack youíre experiencing can help you identify the best course for prevention and resolution.
The three main spoofing attacks to look out for are:
Denial-of-service attacks: In a denial-of-service attack (DoS), a cyber hacker tries to disrupt the service or host connection to make your site or resources unavailable to their intended audience. The attacker will usually use one computer and internet connection to overwhelm and flood a victimís system so they can access their data.
Session hijacking: Session hijacking attacks can use ARP spoofing to steal a session ID and open the door to your private data. This is why using public WiFi in cafes and busy airports can create a vulnerable situation for your data.
Man-in-the-middle attacks: Man-in-the-middle attacks use ARP spoofing to intercept incoming traffic from a legitimate user and modify it to gain access to the session.
Once you know what kind of attack youíve been hit with and whatís going on in your systems, you can determine what course of action to take or how to better safeguard your devices and data.
One way to prevent ARP spoofing from happening in the first place is to rely on Virtual Private Networks (VPNs). When you connect to the internet, you typically first connect to an Internet Service Provider (ISP) in order to connect to another website. However, when you use a VPN, youíre using an encrypted tunnel that largely blocks your activity from ARP spoofing hackers.
The simplest form of certification is the use of static, read-only entries for critical services in the ARP cache of a host. IP address-to-MAC address mappings in the local ARP cache may be statically entered. Hosts don't need to transmit ARP requests where such entries exist. While static entries provide some security against spoofing, they result in maintenance efforts as address mappings for all systems in the network must be generated and distributed.
Software that detects ARP spoofing generally relies on some form of certification or cross-checking of ARP responses. Uncertified ARP responses are then blocked. These techniques may be integrated with the DHCP server so that both dynamic and static IP addresses are certified. This capability may be implemented in individual hosts or may be integrated into Ethernet switches or other network equipment.
Operating systems react differently. Linux ignores unsolicited replies, but, on the other hand, uses responses to requests from other machines to update its cache. Solaris accepts updates on entries only after a timeout. In Microsoft Windows, the behavior of the ARP cache can be configured through several registry entries under HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters, ArpCacheLife, ArpCacheMinReferenceLife, ArpUseEtherSNAP, ArpTRSingleRoute, ArpAlwaysSourceRoute, ArpRetryCount.
To sum it up
All in all, Anti Netcut is a simple utility developed to play the role of a personal bodyguard for the computer. It detects spoofing and takes the required measures to prevent any harm it may cause. However, it cannot and should not be used alone, as its protection is not enough to block malware infections.Conclusion
To conclude Anti Netcut works on Windows operating system(s) and can be easily downloaded using the below download link according to Freeware license. Anti Netcut download file is only 2.6 MB in size.Anti Netcut was filed under the Networking category and was reviewed in softlookup.com and receive 5/5 Score.
Anti Netcut has been tested by our team against viruses, spyware, adware, trojan, backdoors and was found to be 100% clean. We will recheck Anti Netcut when updated to assure that it remains clean.
Anti Netcut user Review
Please review Anti Netcut application and submit your comments below. We will collect all comments in an effort to determine whether the Anti Netcut software is reliable, perform as expected and deliver the promised features and functionalities.Popularity 10/10 - Downloads - 850 - Score - 5/5
Softlookup.com 2023 - Privacy Policy
| Category: | Networking |
| Publisher: | Tools4Free |
| Last Updated: | 23/11/2023 |
| Requirements: | Windows 10 / Windows 8 / Windows 7 / Windows Vista / XP |
| License: | Freeware |
| Operating system: | Windows |
| Hits: | 1400 |
| File size: | 2.6 MB |
| Price: | Not specified |
| Name: * |
E-Mail: * |
| Comment: * |
|